Spytector User Manual
Features and usage
1. Settings preview2. Keylogger outline
3. Install and uninstall
4. Receiving the logs
5. Settings description
6. Security
7. Purpose/Legality
1. Settings preview
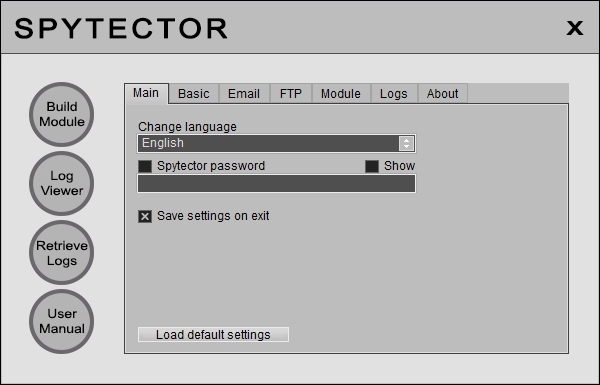
Local Options
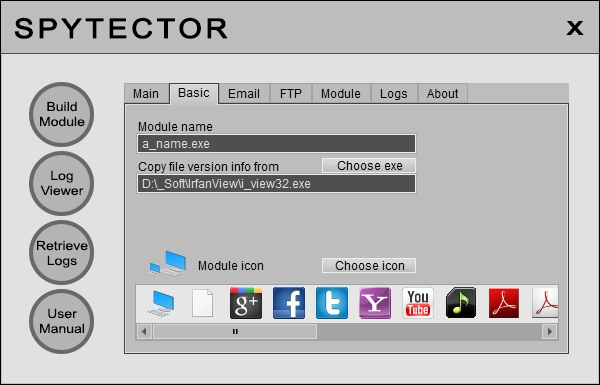
Basic Settings
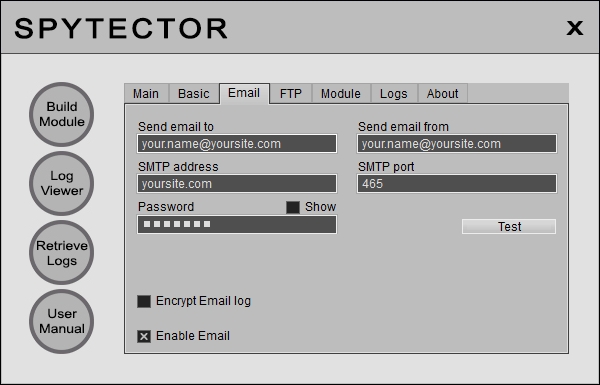
Email Settings
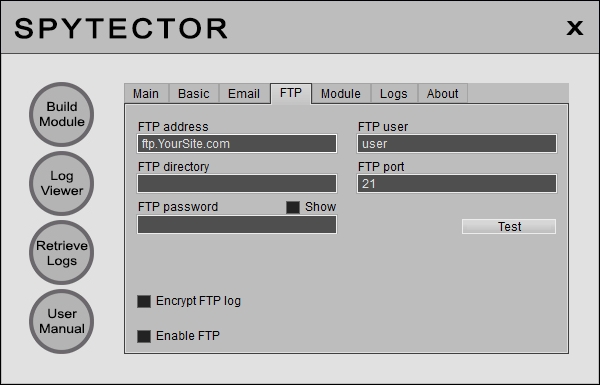
FTP Settings
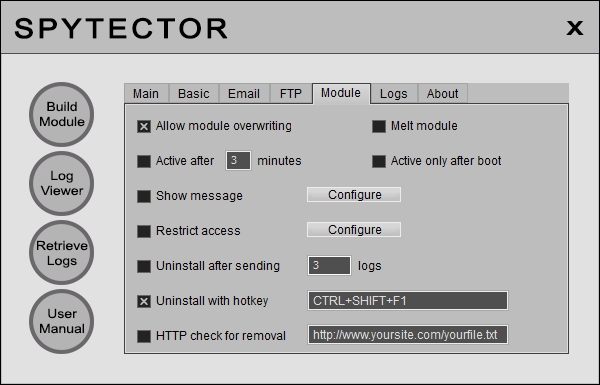
Module Options
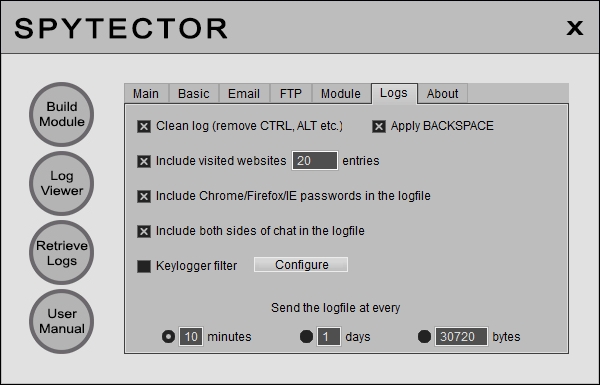
Log Options
2. Keylogger outline
Spytector is made up of 2 programs: the main program ("Spytector.exe") which is used to configure the monitoring options and the "module" file ("module.exe") which has to be installed on your target computer. Of course, the actual monitoring program (keylogger) is the "module" file.
Spytector usage is straightforward: configure the desired settings on the main Spytector program, build the "module", run the "module" (with a regular doubleclick) on the target computer. The target computer can be either your local computer or a remote one (by example at your office, or your kid's laptop etc.).
The same keylogger ("module") can be installed on all your computers (no limit). Our licensing is per user, not per computer. All you need is 1 license and all your computers may be monitored.
Spytector keylogger is the most undetectable keylogger you can buy on the Internet and we guarantee it's undetected when scanned with the following antivirus programs: Norton AV, Kaspersky AV, Malwarebytes, McAfee, AVG, Avast, Panda, TrendMicro. While the *full* version is undetected, the *trial* version (publicly available on our website's download section) is detected by all the AV programs so you should temporarily disable your AV for proper testing.
Spytector is fully compatible with all the Windows operating systems versions in use (i.e. Windows 2k, XP, Vista, Windows 7, Windows 8, Windows 10, Windows 11) and works on both 32bit and 64bit.
3. Install and uninstall
At the first run of Spytector, the user is asked to agree to the License terms (EULA). The agreement is mandatory, otherwise the program cannot be used.
Spytector is offered as a standalone/portable application - it doesn't need administrative privileges and won't create any shortcuts on Desktop, Start Menu, Add/Remove Programs. The portable Spytector will work from wherever it's placed.
Being a portable application (no entries in the Add/Remove Programs list in Control Panel), the uninstall can be done by simply deleting the files.
For the "module" (the actual keylogger), the easiest way to uninstall it is with the hotkey (the default hotkey is CTRL-SHIFT-F1). The hotkey uninstall option is enabled by default.
4. Receiving the logs
The reports/logs can be retrieved from the main Spytector program ("Retrieve Local Log" -> "Automatically Retrieve The Logs") or the keylogger can be configured to send the logs to your email/FTP account.
The logs can be viewed in "Log Viewer" - an in-built utility. The different log sections are colored, so the user can easily see the monitored activity. Initially, all the sections (Passwords, URL history, Boot, Keystrokes etc.) are put together, with the Passwords on top. From the upper right combo box, the user can choose different sections to view. The log can be searched for specific keywords and the search can be executed upwards, downwards, case sensitive and/or for whole words.
The email feature (see Email Settings) can work with most email providers. By example you can use a free Yahoo account on "Send Email From" and a Gmail account on "Send Email To". Of course, you'll receive the logs at the account configured on "Send Email To". The Yahoo's SMTP is smtp.mail.yahoo.com and the required port number is 465 (for SSL connections). Even if the keylogger can work with free email providers, it's better to use a paid-for email account. The paid accounts are more reliable and the risk to have your account blocked or the logs filtered is almost zero. The same goes for the FTP feature (see FTP Settings). While the keylogger can work with almost all the FTP providers, the free FTP accounts may have restrictions. The email/FTP accounts can be purchased from us or from other providers.
5. Settings description
By default, the keylogger is preconfigured with values that provide common functionality. The email and FTP settings, used for receiving the logs, are mandatory only in the case the keylogger is installed remotely and you don't have access to your monitored computer. If you have permanent access to the monitored computer, the logs can be easily retrieved from the main Spytector (use "Retrieve Logs" -> "Automatically Retrieve Logs").
On the Main Settings panel you are able to password protect Spytector (useful if more people have access to your computer), change the interface language (English, French, Portuguese) and configure Spytector to remember your settings. There is also the option to restore all the predefined settings ("Load Default Settings" button).
On Basic Settings you are able to set the keylogger icon, the executable version information and the name used by the "module" after installation. The executable version information and the icon are very important if you are concerned about antivirus detections. Some antivirus programs could detect the programs with small icons and no version information. Spytector is able to add to the "module" any icon, so our advice is to use an icon bigger than 50KB. When you build the "module", use the option to copy the file information from another executable (by example a graphic program like Irfanview) - this will help on avoiding some AV detections.
The Email Settings and FTP Settings have been presented in Receiving the logs section.
On Module Options panel you're given the choices to customize the "module" even more: - overwriting (a new "module" can be run over the already installed "module") - melt option (the initial "module" deletes itself after the first run) - delay activation (after a specified time interval or after the system reboot) - warning message configuration (the "module" displays the warning at the first run) - uninstalling (after some logs are sent or when a hotkey is pressed) - access restriction (the monitored user won't be able to access the specified websites and programs) - uninstall by checking an Internet page (if the Internet page is valid/exists the "module" will uninstall itself)
On Log Options you can configure a keylogger filter (the keylogger is active only when the window title/caption contains the desired keyword), set the option to receive cleaned logs (without dead keys and navigation keys) and apply BACKSPACE (the last typed characters are deleted from the log when BACKSPACE is used), option to retrieve the passwords stored in browsers, interception of of messenger conversations, inclusion of URL history, option to receive the logs at a specified size or once a day or even at a minutes interval.
6. Security
Spytector is a professional keylogger that is completely undetectable. During monitoring sessions Spytector is invisible and cannot be seen or easily detected by any user! With Spytector running all information will be captured on your PC and recorded in complete stealth mode. This means no worrying about someone discovering the keylogger running during monitoring sessions!
Spytector is cloaking itself in system, being run inside operating system services. The keylogger cannot be seen in the Task Manager, Add/Remove Programs Menu, Start Menu, Taskbar and is able to bypass the protections implemented in new Windows systems (UAC - User Account Control). That means you don't have to make any modification to your system to allow the keylogger!
What separates Spytector keylogger from the many others offered on the internet? What makes Spytector stand out from the competition? It's the undetectability - the developers' commitment to build undetectable versions on a daily basis! While the other keyloggers on the market are updated monthly (or less often) and the same build is shared by a lot of users, we build Spytectors almost daily. Each Spytector build is shared only by a very few users and due to that the probability of detection is kept as low as possible. Yes, that implies more work for us but we stand behind our claim of delivering the most undetectable keylogger in the world. Many of the monitoring programs available on the market are detected and the ones claimed to be undetected are updated monthly or even less often...
Spytector keylogger is the most undetectable keylogger (FUD keylogger) you can buy on the Internet and we guarantee it's undetected when scanned with the following antivirus programs: Norton AV, Kaspersky AV, McAfee, Panda, AVG, Avast, TrendMicro. While the *full* version is undetected, the *trial* version (publicly available on our website's download section) is detected by all the AV programs so you should temporarily disable your AV for proper testing.
7. Purpose/Legality
There are many situations when you need to use an undetectable keylogger: you need to know what are your employees doing at work, you suspect someone may be misusing your PC, you need to know with who is your spouse chating online, you need to know what websites are your kids visiting etc. Spytector keylogger is the best solution for these purposes, it runs completely invisible and undetectable, so no one except you will know it's running on the monitored computer.
Spytector is not intended for hacking or any other malicious or unauthorised usage. Spytector keylogger must be used in a lawful manner. You must be the authorized system administrator, the owner of the computer to be monitored or you must have the permission from the owner of the computer to install the keylogger. In the case you are not the system administrator, the owner of the computer or do not have the permission from the owner of the computer, you don't have the right to install our monitoring software. If you intend to monitor your employees, you could be legally obliged to inform your employees that they are being monitored. Before using Spytector it is strongly recommended to check the local laws in your district/country.
We will not protect or passively condone illegal activities in violation of state or federal laws.